API key
An API key is designed for server-to-server communication and should not be shared with or used by end-users directly. It serves as a secure credential to authenticate and authorize requests made to the server API. Key Features:- The API key is permanent and does not have an expiration date.
- It grants full permissions to perform any action within the server API.
- To authenticate requests using the API key, include it in the request headers as follows the example:
{API_KEY} with the actual API key value.
- Request Execution on Behalf of a User
{USER_ID} with the unique identifier of the QuickBlox user.
Security Considerations
To maintain the security and integrity of the API key, follow these best practices:
- Keep the API key confidential and do not share it with unauthorized individuals.
- Transmit the API key securely over HTTPS.
- Regularly review and audit the server-side access and permissions associated with the API key. If an API key is compromised or suspected of being compromised, replace the API key immediately for further action.
Application vs User session token
A token is a piece of data identifying a user or application and providing temporary access to QuickBlox Server API. The token is valid only within the session it was generated. The session gets expired in 2 hours after the last request to the Server API. A session token is obtained via Create Session request having/session.json endpoint. Once a token is received, it becomes a part of each request and is placed within its header.
There are two types of tokens: application session token and user session token. The application session token is limited to read-only permissions preventing changes to application data while the user session token is not restricted in permissions and allows for making edits to application data.
| Session Token Type | Description |
|---|---|
| Application session token | This kind of access token is needed to read the app data. Has only READ access to resources. The expiration time after the last Server API request is 2 hours. |
| User session token | The user token is the most commonly used type of token. This kind of access token is needed any time the app calls a Server API to read, modify or write a specific user’s data on their behalf. Has READ/WRITE access to resources. The expiration time after the last Server API request is 2 hours. |
Want to change session expiration time? This option is available for Enterprise Plan only. Contact the sales team.
Signature generation
Use a signature mechanism to verify the contents of the Create Session request on the QuickBlox server. The signature is generated using the HMAC-SHA cryptographic hashing algorithm. Then it is sent in the session creation request to verify the end-user. The inputs to a hashing algorithm include:- A normalized string. The string is formed using the
parameter=valuepairs that should be sorted alphabetically by their text value and separated by the&character. Use the parameters of the create session request to form the string. - An authorization secret. The secret is known as a cryptographic key and is used to compute the HMAC.
- A hashing algorithm. The cryptographic hash function.
For Basic, Startup, Growth plan, and HIPAA Cloud users
The SHA1 hash algorithm is used to generate a signature.For Basic, Startup, Growth plan, and HIPAA Cloud users
- By default, the SHA1 hash algorithm is used to generate a signature.
- Contact our sales team if you need to change SHA1 to SHA256.
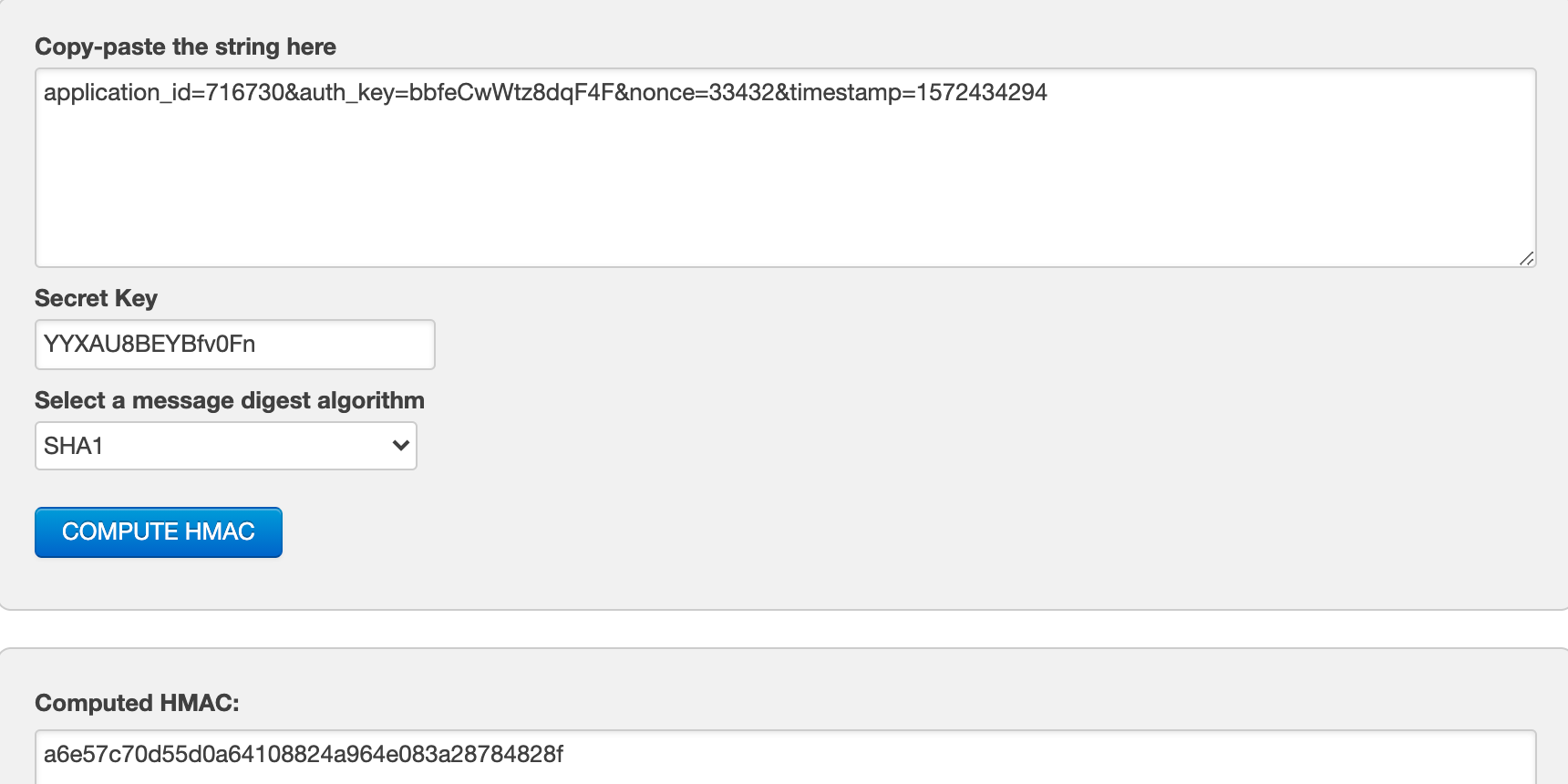
- Open the HMAC-SHA generator. For example, you can use this one.
- Compose a normalized string from
parameter=valuepairs. For example: application_id=716730&auth_key=bbfeCwWtz8dqF4F&nonce=33432×tamp=1572434294 - Enter the authorization secret(secret key).
- Choose SHA1 hashing algorithm.
- Generate the signature. Your screen should look similar to the screenshot below: