Recommended workflow
Application - web or mobile application that integrates QuickBlox. Identity provider (IdP) - service that authenticates and verifies user credentials, it’s external to QuickBlox. IdP_user_ID - user ID in external service. IdP_token - access token to external service.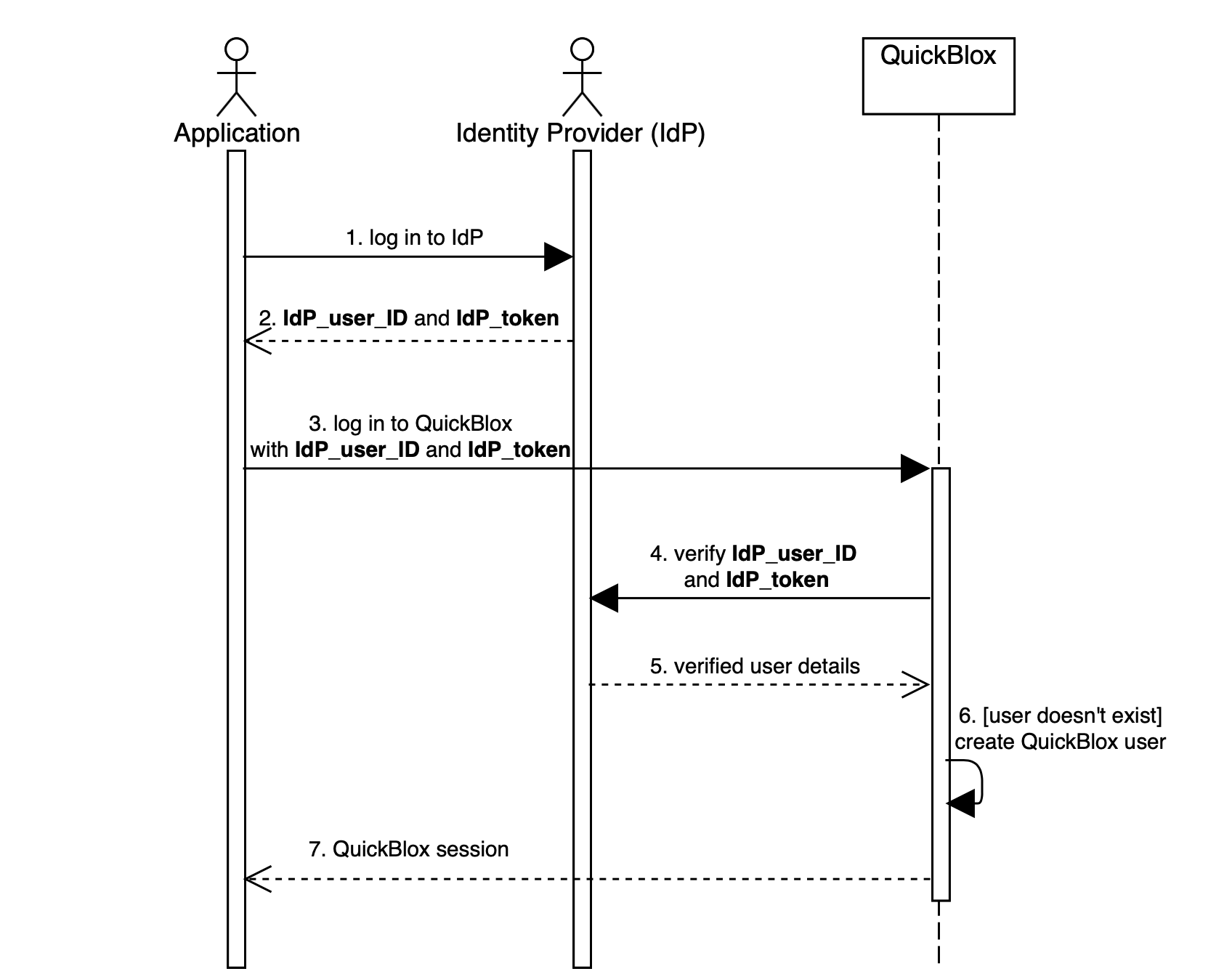
- The application logs in user to the identity provider.
- The identity provider returns the IdP_user_ID and IdP_token.
- The application logs in user to QuickBlox. IdP_user_ID and IdP_token must be set as
user[login]anduser[password](see Create Session). - The QuickBlox server sends IdP_user_ID and IdP_token to identity provider for verification.
- The identity provider checks that credentials are correct and sends user details back to QuickBlox server.
- The QuickBlox server parses response from IdP and creates a new QuickBlox user if it doesn’t exist.
- The QuickBlox server sends a user session token back to the application.
Step 1: Create verification endpoint
Identity provider must provide interface for QuickBlox to verify users - verification endpoint. This endpoint will be triggered every time when user tries to log in to QuickBlox API. There are no strict rules how endpoint must look. The only requirement it must receive some credentials, for example, token, and return unique identifier of the user. You can send additional information about user that can be parsed into QuickBlox user, for example, full name or email, the full list is available here. Example: In this example,IdP_user_ID and IdP_token are credentials, user.id is unique identifier.
HTTP
JSON
NoteIf identity provider returns an error QuickBlox will resend the error as is to the application.
Step 2: Configure CIdP
Once verification endpoint is set and running, you can configure QuickBlox CIdP.- Go to the Dashboard => YOUR_APP => Overview page.
- Locate the Custom Identity Provider groupbox at the bottom of the page.
- Check Enable custom Identity Provider authentication.
- Fill in the API URL field with your verification request URL.
- Choose a request type from the dropdown: GET or POST.
- Fill in Request headers or Request params.
- Fill in Response params.
- Click the Update button. Now users authenticate via your Identity Provider.
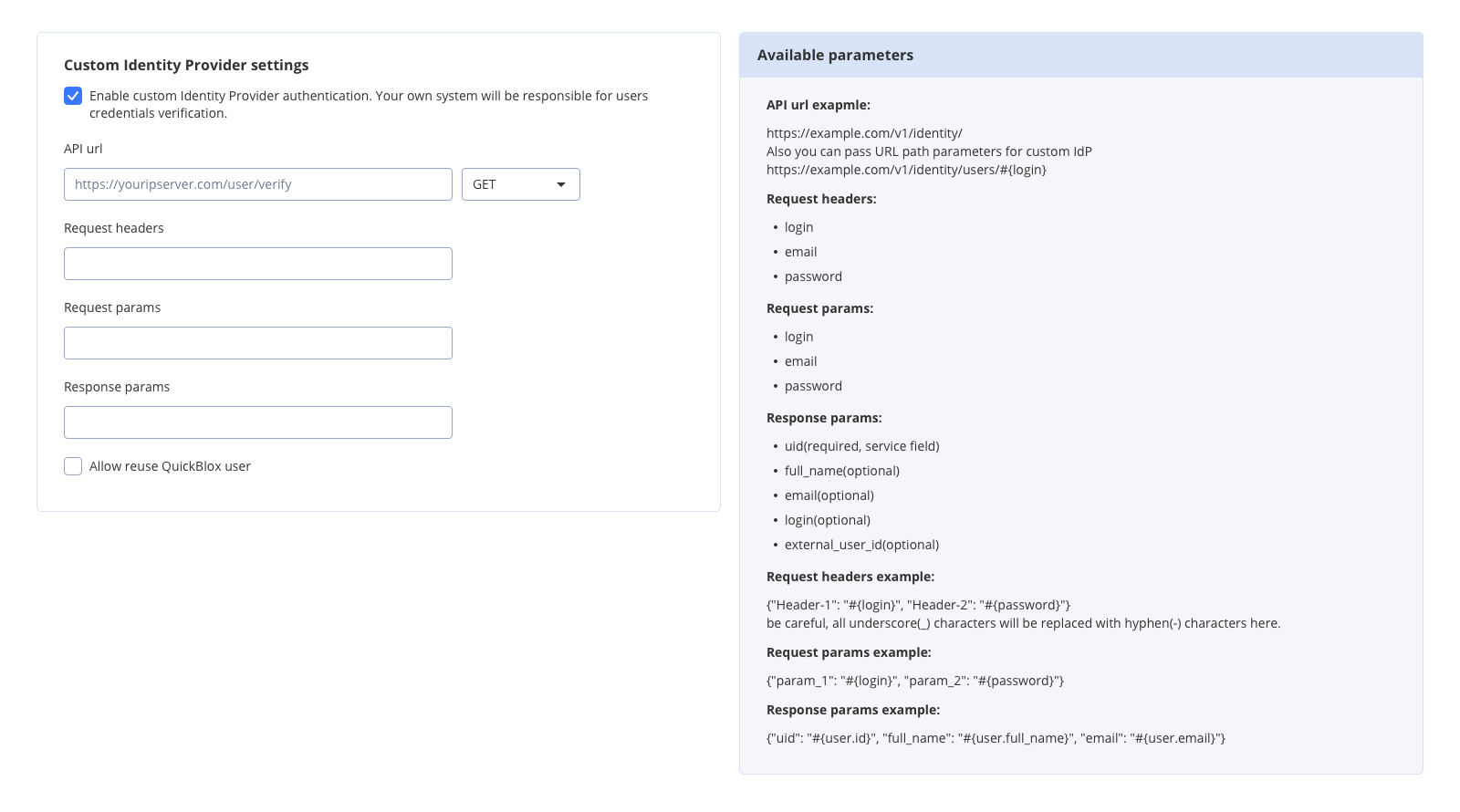
API URL
URL of the verification request. It will be triggered every time when user tries to log in to QuickBlox API. Example: https://youripserver.com/users/identityRequest headers
Headers of the verification request. Header name can be any, as a value you can set one of available variables. Here you define how to map params of QuickBlox Create Session request to headers of your verification request. You can pass data via request headers or request params, both are valid and optional. Format:{"Header-1": "#{variable-1}", "Header-2": "#{variable-2}"}
*All underscore(_) characters will be replaced with hyphen(-) characters here.
Example:
{"IdP_user_ID": "#{login}", "IdP_token": "#{password}"}
Allowed variables:
| Variable | Type | Description |
|---|---|---|
| login | string | Value of user[login] (see Create Session). |
| password | string | Value of user[password] (see Create Session). |
| string | Value of user[email] (see Create Session). |
Request params
Params of the verification request. Param name can be any, as a value you can set one of available variables. Here you define how to map params of QuickBlox Create Session request to params of your verification request. You can pass data via request headers or request params, both are valid and optional. Format:{"param_1": "#{variable-1}", "param_2": "#{variable-2}"}
Example:
{"IdP_user_ID": "#{login}", "IdP_token": "#{password}"}
Allowed variables:
| Variable | Type | Description |
|---|---|---|
| login | string | Value of user[login] (see Create Session). |
| password | string | Value of user[password] (see Create Session). |
| string | Value of user[email] (see Create Session). |
Note
GET request will use query params.
POST request will use body params.Response params
Response parameters are received as a result of the verification request. Here you define how to map received data to QuickBlox user. QuickBlox will create user session if response is valid and parsed. New user will be created if UID is not found in QuickBlox database. Format:{"qb_user_field_1": "#{param_1}", "qb_user_field_2": "#{param_2}", "qb_user_field_3": "#{param_3}"}
Example:
{"uid": "#{user.id}", "login": "#{user.login}", "full_name": "#{user.full_name}", "external_user_id": "#{user.id}"}
JSON
| Field | Type | Required | Description |
|---|---|---|---|
uid | string | yes | Unique identifier. Hidden system field that links QuickBlox user with external system. |
login | string | no | User’s login (see Users). Generated based on UID if not specified. |
email | string | no | User’s email (see Users). Empty if not specified. |
full_name | string | no | User’s full name (see Users). Empty if not specified. |
external_user_id | int | no | ID of user in external system (see Users). Empty if not specified. |
Allow reuse QuickBlox user
Any user registered with CIdP has UID. This system field links QuickBlox users and external users. If UID doesn’t exist in the QuickBlox database - a new user will be created. This checkbox tells how to act when external service responds with UID that is already in use and QuickBlox user exists:- If checked - QuickBlox session is created with an existing user.
- If not checked - QuickBlox session is created with a new user, UID will be assigned to the new QuickBlox user.
Step 3: Implement app authentication
On the application side you must implement regular login/password authentication. It’s important to set your credentials intologin and password parameters, for example, put IdP_user_ID to login and IdP_token to password.
This is done for easy migration of applications that are already published on Apple Store and Google Play.
- cURL
- JavaScript SDK
- iOS SDK
- Android SDK
Step 4: Implement Chat connection
When CIdP is enabled you must connect to chat with QuickBlox user ID and session token.- JavaScript SDK
- iOS SDK
- Android SDK